If digits of my age are reversed you will get my son's age…
June 11, 20123 basket puzzle (Apple/Orange Puzzle)
June 11, 2012'man-in-the-middle' attack on data being transfered over Network
There are multiple types of attack which are possible on the data when the data is being transferred over the network from one machine to another. One such attack is called ‘Man-In-The-Middle’. What is it and what are the different types? (Other type of attacks may be ‘IP Spoofing’, eavesdropping etc.)
Solution:
A man-in-the-middle attack occurs when someone is actively monitoring, capturing, and controlling the communication between two computers transparently (without the knowledge of sender or receiver). For example, the attacker can modify the data, replay it, or just listen to it.
When computers are communicating at low levels of the network layer, the computers might not be able to determine with whom they are exchanging data.
Man-in-the-middle attacks are like someone assuming your identity in order to read your message. The person on the other end might believe it is you because the attacker might be actively replying as you to keep the exchange going and gain more information.
Following pictures, represent the effects of Man-In-Middle Attack:
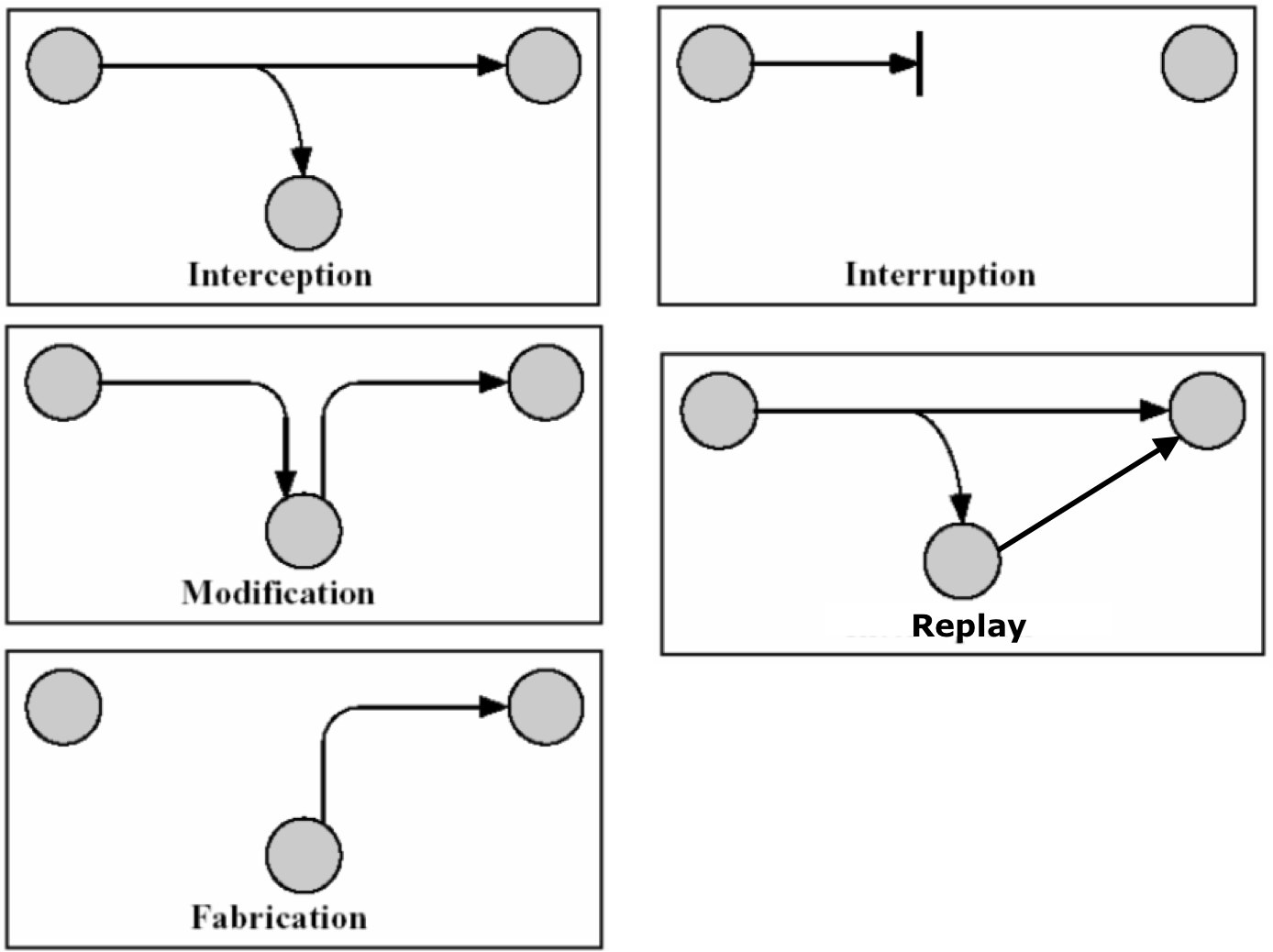
So the Man-In-The-Middle may be
- Interception: Just listening to your communication. Imagine someone listening to the National secrets.
- Interruption: Receiving the messages and disallowing the receiver to receive them. The sender will believe, that the receiver has received the message but the receiver has not received it. Suppose you want to fire a missile, but the missile software is not receiving your commands, and worst is that you think missile is fired 🙂
- Modification: The middle man receives the message, modifies it and then send to the actual receiver. Imagine if the target of missile is changed to your country itself :))
- Replay: The middle man may receive your data.. and then keep sending it to the receiver (The receiver will think you have send the data again).. More missiles getting fired then you ordered 🙂
- Fabrication: The middle man will just fabricate a new message and will send it to the receiver. The receiver will believe that the message came from the sender. Now the last one, Imagine Missile being fired to your friendly nations 🙂
